Have you ever wished you could send messages where there’s no cell service or when roaming fees are sky-high? Meshtastic makes it possible. This open-source project lets anyone create a mesh network using affordable LoRa radio modules.
It’s like setting up a mini-internet that works anywhere. Whether you’re hiking in remote areas, attending a packed festival where networks are overloaded, or like us spending time off-grid on a remote island, Meshtastic has you covered.
At its core, Meshtastic combines two technologies: LoRa (Long Range) radio for communication and Protocol Buffers (protobuf) for efficient data packaging. Together, they create a system that sends messages over several kilometers while using minimal power.
In this post, we’ll explore how Meshtastic works behind the scenes—how it cleverly routes messages, manages power use, and what makes its mesh networking approach unique. By the end, you’ll understand what makes this technology tick, even if you’re new to radio communications.
How Meshtastic Works: The Building Blocks
A Meshtastic node combines a LoRa radio module with a microcontroller (usually an ESP32 or RAK Wireless board) running the Meshtastic firmware. Most setups rely on a phone running the Meshtastic app to act as your interface for typing and reading messages.
Some devices are self-contained, though that’s more the exception than the rule.
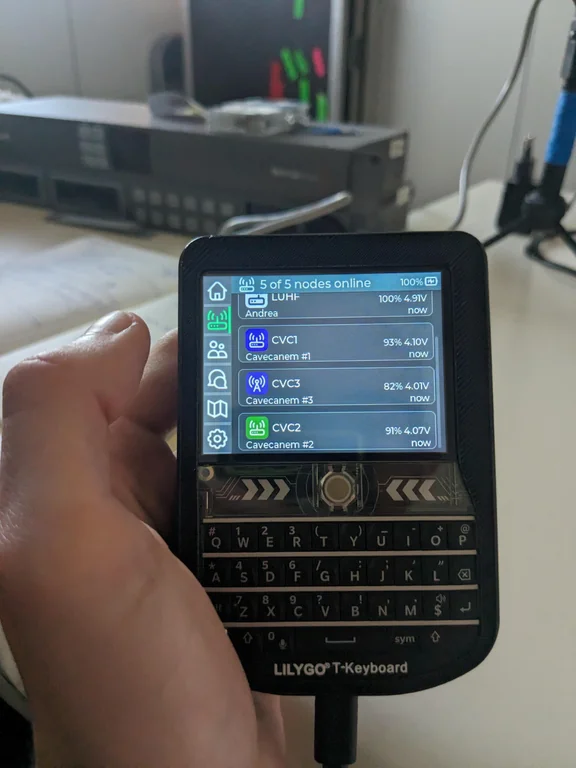
The LoRa Magic
LoRa (Long Range) serves as the backbone of Meshtastic, using a unique technique called chirp spread spectrum modulation. Imagine it like Silbo Gomero, the whistled language used in the Canary Islands. Just as people in the islands communicate across valleys with modulated whistles, LoRa signals use “chirps”—waves sweeping up or down in frequency—to carry messages across vast distances.
Just like those whistled messages can reach across valleys, LoRa chirps travel long distances by spreading the signal across multiple frequencies. Even if there’s background noise, these chirps still stand out.
Using the standard sub-GHz LoRa modules, these chirping signals can travel several kilometers, even in urban areas, and much further in open spaces. Newer 2.4 GHz LoRa modules offer higher data rates but at a shorter range, making them best for closer setups.
Channel Settings Made Simple
Meshtastic simplifies radio parameters with easy presets when you create a channel. Each preset suits different situations:
- short_fast: Great for quick messaging between nearby nodes, like within a campsite. Fast transmission but limited range.
- medium_fast: Balanced for general use in a smaller area.
- long_fast: That’s the safe default, extending range while keeping reasonable speed.
- long_moderate: Stretches range further, though messages may take longer, often used in urban areas.
- very_long_slow: Maximum range for far-off nodes, though expect a delay in message arrival.
Under the hood, these presets adjust radio settings like bandwidth (frequency sweep), spreading factor (chirp duration), and coding rate (error correction). For instance, “very_long_slow” maximizes range using the highest spreading factor (SF12) and narrow bandwidth, while “short_fast” prioritizes speed with a lower spreading factor and wider bandwidth.
Smart Message Handling
When you type a message in the Meshtastic app, here’s what happens:
- Protocol Buffers compact your message for efficient transmission.
- The device adds routing info (origin and destination).
- The LoRa radio sends it out.
- Other nodes receive it and may relay it, extending its reach.
Playing Nice with Radio Rules
Meshtastic operates in ISM (Industrial, Scientific, and Medical) bands, where strict regulations apply. For example, in Europe, devices may transmit only 1% of the time on the 868 MHz band—roughly 36 seconds per hour. Meshtastic carefully manages message size and transmission times, and the app displays the duty cycle to help you stay within legal limits. These restrictions make protobuf’s data efficiency even more essential.
Making Messages Tiny with Protocol Buffers
This is where Protocol Buffers (protobuf) shine. They pack data efficiently, almost like vacuum-sealing your camping gear instead of stuffing it in a bag. If you’ve ever played online games, you’ve likely used protobuf as a go-to for quick, efficient data updates.
Meshtastic defines structured message formats in protobuf, resulting in a streamlined data packet. Instead of sending messages as raw text, Meshtastic assigns a small identifier to each field in a message and transmits only non-empty fields. Here’s how protobuf keeps data compact:
- Transmitting only fields with data
- Using variable-length encoding (smaller numbers take fewer bytes)
- Packing repeated fields efficiently
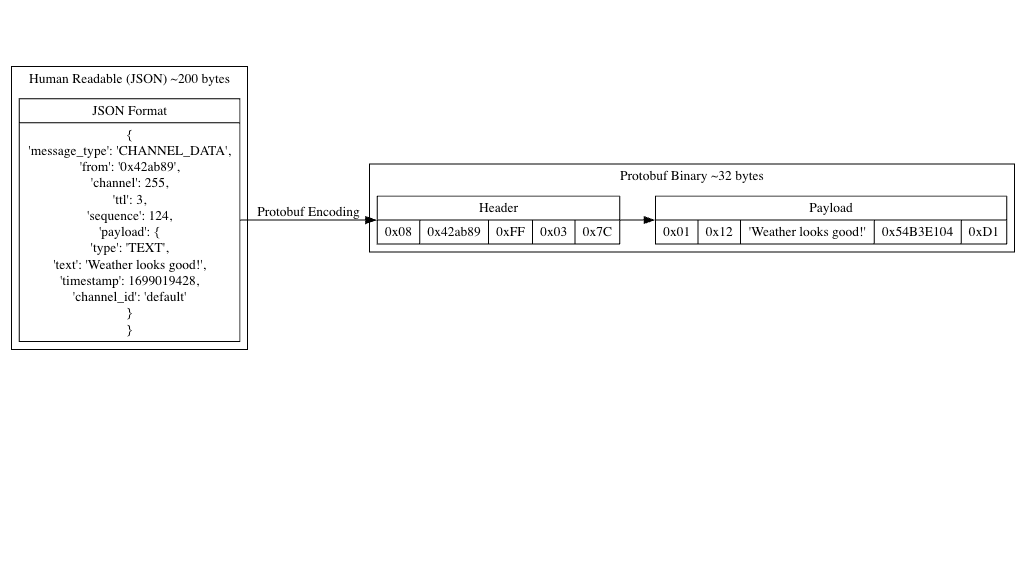
For example, a message that might require 100 bytes as JSON could reduce to around 20–30 bytes with protobuf—an essential savings given the airtime limitations!
How Messages Find Their Way
Picture this: you’re a family is anchored in a bay. Parents are hiking inland, kids are visiting friends on another boat, and you’re on your boat (“Boat Node”) in the middle. When the kids send, “What’s for dinner?”, Meshtastic uses “flood routing” to make sure it reaches everyone.
Here’s how it works:
- The kids’ node sends the message.
- Boat Node receives it and decides, “This is new—let’s pass it on!”
- Boat Node rebroadcasts the message.
- Parents’ node, unable to hear the kids directly, receives it through Boat Node.
- If another node rebroadcasts the same message, other nodes ignore it—they’ve seen it before!
This “flooding” approach means messages traverse all possible paths through the network, ensuring they arrive as long as there’s a link between nodes, even if locations shift.
Flooding and Acknowledgments (ACKs)
Meshtastic’s “flood routing” ensures messages reach their destination, especially in dynamic environments where nodes may move in and out of range. But flooding alone doesn’t guarantee delivery, which is where acknowledgments (ACKs) come into play.
In a mesh network, flooding means that when a node receives a new message, it rebroadcasts that message so nearby nodes can pick it up. This way, even without a direct line between sender and receiver, the message can make it through multiple hops.
However, with flooding, there’s no immediate confirmation that the intended recipient received the message. This is where ACKs step in. When a node receives a message intended for it, it sends back an acknowledgment—essentially a “Got it!”—to the sender. This lets the sender know the message arrived successfully, which is crucial when coordinating over long distances.
Meshtastic balances message reliability with network efficiency by selectively using ACKs. For critical messages where knowing whether the message got through is essential, Meshtastic uses ACKs. But for less critical broadcasts, it can skip the ACKs to save airtime and battery, as each additional message (even an ACK) consumes power and airtime.
This dual approach allows Meshtastic to be both resilient and efficient. Flooding helps messages spread widely, while ACKs ensure critical messages don’t get lost in the mix. Together, they enable communication even when connectivity is less than ideal.
Battery Efficiency
Battery life is a key consideration in Meshtastic networks, especially for remote and off-grid applications where your charging options are limited. Meshtastic operates efficiently, conserving battery while maintaining connectivity.
The hardware layer starts with LoRa radios, which are inherently low-power. LoRa’s energy footprint is a fraction of what traditional cellular or Wi-Fi modules require, making it a practical choice for low-power, long-distance communication.
On the software side, Meshtastic uses several strategies to reduce power draw:
- Sleep modes: When idle, nodes enter a low-power state. They spend most of their time in this sleep mode, significantly extending battery life.
- Duty cycling: Nodes wake up at regular intervals to check for messages or send data. By keeping these active periods short, Meshtastic limits overall energy consumption.
- Message filtering: Not all messages require an acknowledgment, and not every node needs to rebroadcast a message. This filtering reduces unnecessary transmissions, saving power.
- Data compression: Protocol Buffers (protobuf) compact the data, reducing transmission times and power needed per message. With smaller packets, the radio stays on for less time, minimizing power use.
These combined strategies mean that a Meshtastic node can operate for days or weeks on a single charge, depending on the specific hardware and use case. By prioritizing low-power modes and efficient transmission, Meshtastic maximizes battery life for long-term deployments in challenging environments.
Security Considerations
In any mesh network, security is critical to ensure that communications are private and that the network remains robust against misuse. Meshtastic integrates several security measures, including channel encryption, privacy features, and mechanisms to address potential vulnerabilities.
Channel Encryption
Meshtastic uses encryption to secure all communications between nodes. By default, messages sent over Meshtastic channels are encrypted using AES-256, a widely adopted standard in secure communications. This means the device scrambles each message before transmission, and only nodes with the correct channel key can decrypt and read the data.
Each channel is configured with a unique AES key. When setting up a Meshtastic network, users generate a shared key that each participating device must have to join the network. This ensures that only authorized devices can decrypt and participate in the communication on that channel. Securely sharing the AES key with trusted users is essential to prevent unauthorized access.
In practice, this approach effectively prevents external devices from intercepting or tampering with messages, as they lack the AES key required to decrypt the data.
Privacy Features
Beyond encryption, Meshtastic offers several privacy-oriented features to enhance security within the network:
- Device Anonymity: Meshtastic does not transmit identifiable device information. Instead, each device uses randomized identifiers in message headers, ensuring that individual devices cannot be easily tracked within the network.
- Message Obfuscation: Meshtastic minimizes and obfuscates messages where possible, meaning that even if intercepted, they appear as compact, unreadable data.
- Optional Broadcasting Controls: Users can configure channels with different broadcast settings, limiting how widely messages are relayed. This helps prevent unnecessary message propagation in sensitive networks.
Potential Vulnerabilities and Mitigations
Despite these security measures, certain vulnerabilities are inherent in any mesh network. Here’s a breakdown of some potential risks in Meshtastic and how they are addressed:
- Replay Attacks: Since Meshtastic messages are relayed across multiple nodes, a malicious actor could capture and replay a message. To mitigate this, Meshtastic includes unique message IDs and timestamps to detect duplicate messages and prevent replays within the network.
- Denial of Service (DoS): A malicious node could theoretically flood the network with repeated transmissions, overwhelming other nodes. Meshtastic uses duty cycling and message filtering to limit excessive rebroadcasting, reducing the impact of DoS attempts. Additionally, nodes can ignore repeated messages or those exceeding certain thresholds.
- Key Management Risks: If you share the AES channel key insecurely or it falls into the wrong hands, unauthorized devices could decrypt and access the channel. Secure key-sharing practices are essential; ideally, share the key only over secure channels or in person to avoid interception. Periodically rotating the channel key also limits exposure over time.
- Physical Compromise of Devices: Since Meshtastic nodes are often deployed in the field, there’s a risk of devices being physically accessed by unauthorized users. To counter this, you can configure Meshtastic devices to store minimal information locally, limiting potential data exposure if a device is lost or stolen.
By combining robust encryption, privacy-oriented design, and specific protections against common vulnerabilities, Meshtastic provides a secure foundation for off-grid and remote communications. However, best practices—such as secure key sharing, routine key updates, and careful network configuration—are essential to maintaining a secure Meshtastic network.
Access to a Meshtastic network relies on possession of the shared AES key; there is no user-specific authentication. Any device with the correct key has full access to the channel, so securely distributing and limiting access to the key is essential.
Conclusion
Meshtastic opens up a world of communication possibilities when traditional networks are unavailable or impractical. By leveraging LoRa technology, efficient data handling with Protocol Buffers, and thoughtful features like robust security measures, it provides a versatile platform for a wide range of applications. Whether you’re an outdoor enthusiast, part of a remote team, or simply interested in off-grid communication, Meshtastic offers a user-friendly and powerful solution.
As an open-source project, Meshtastic continues to evolve with contributions from its community. This collaborative effort ensures that the technology adapts to new challenges and user needs, making it an exciting space to watch or get involved in. If you’re intrigued by the possibilities, consider exploring Meshtastic further and joining the growing network of users and contributors.
Sources:
https://meshtastic.org
https://www.reddit.com/r/meshtastic/
